Highlights:
- Increased Cyber Activity: Various hacktivist groups, aligning with different geopolitical interests, have intensified their cyber operations aiming to influence the narratives and disrupt online entities associated with Israel.
- Rise in attacks: Check Point Research noted an 18% rise in cyberattacks targeting Israel recently. Specifically, there’s a marked increase in attacks on the government/military sector – a 52% surge compared to the weeks leading up to October 7.
- Diverse Cyber Threats: The cyber threats are multifaceted, ranging from Distributed Denial of Service (DDoS) attacks by hacktivist groups to hack and leak activities against Israeli websites.
- Emerging Concerns and Players: The article underlines three escalating trends that might intensify the cyber conflict: Russian-affiliated hacktivist groups shifting their focus to Israel, the introduction of Iranian government-backed hacktivist groups, and the participation of cybercriminals eyeing financial gains amidst the conflict. Moreover, sophisticated cyber actors with significant capabilities are entering the scene, heightening risks and tensions in the cyber battleground.
On October 7th, at 6:37 AM, Hamas invaded Israel, triggering significant unrest. Within an hour, by 07:33 AM, the Russian-affiliated group, Anonymous Sudan, purportedly claimed responsibility for potentially disabling an Israeli civilian app designed to alert citizens about missile attacks.
Background
The war that began on the morning of October 7 between Israel and Hamas, known as “Iron Swords”, has also attracted the attention of many threat actors in cyberspace. Much like the Russian-Ukrainian war, there are many individuals and groups trying to leverage cyberspace as an added battlefield, aiming not just to inflict harm but often to orchestrate information campaigns and mould global narratives.
The cyber domain mirrors global diplomatic alignments. With both Russia and Iran publicly supporting Hamas, various Middle Eastern, Islamic, and Russian-affiliated hacktivist groups began reporting hundreds of attacks on Israeli digital entities. However, as of this writing, the effects of these attacks on Israel and affiliated entities have been minimal.
Data collected from Check Point sensors shows that as the war continues, cyberattack attempts increase. During the past few days, Check Point Research observed an 18% increase in cyberattacks on targets in Israel, compared to the first few days of the war. We see a special focus on the government/military sector, with a 52% increase in the number of cyberattacks compared to the average in the weeks before October 7. The global trend in this specific sector shows a 4% decrease in the same timeframe.
This analysis delves into cyber activities as shared by self-proclaimed collectives on platforms like Telegram, the Dark Web, and various open-source intelligence (OSINT) channels.
So far, only a handful of attacks have had a tangible impact. However, three evolving trends that could turn the tide of the cyberwar against Israel are becoming evident:
1. Russian-affiliated hacktivist groups are now focusing on Israel
2. Iranian government-backed hacktivist groups are entering the conflict
3. Opportunistic cybercriminals are exploiting the war to launch ransomware attacks
DDoS Attacks
Since the war began, we have registered hundreds of claims of DDoS attacks by dozens of hacktivist groups. Active groups in this area include pro–Islamic groups like “Ghosts of Palestine”, “Team_insane_Pakistan”, and more. The impact of the vast majority of those attacks was very limited in terms of disruption, as these were executed against either very small websites in Israel or lasted for mere seconds to minutes.
Claims of DDoS attacks have included government entities and major companies, such as the Bank of Israel, the Cellcom cellular company, the Israeli Parliament (known as the Knesset), and more. However, most disturbances had only minor effects, if at all.
One relatively successful DDoS attack has been against the Jerusalem Post website desktop version and was claimed by both Team_insane_Pakistan and Anonymous Sudan. Disruptions to the Jerusalem Post website continued for approximately two days.
Hack and Leak and Disruptive Activities
Since the beginning of the war, multiple claims of hack-and-leak, and defacement activities against Israeli websites and organizations have been posted on various Telegram channels. However, most of the cases have been proven to be reposts of old leaks, or of publicly available data. The successful cases have mostly been against very small websites and organizations.
Of the claimed activities in this area, the most noteworthy are the “Ono Academic College” hack and leak, and the hacking of electronic billboards.
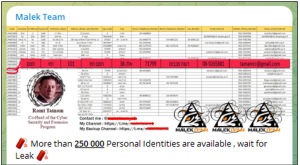
On October 8, a new Telegram channel belonging to a previously unknown group called “Malek Team” appeared and posted claims of hacking into “Ono Academic College”, a private college in Israel. They displayed personal data allegedly stolen from staff and students, including campus CCTV videos. The college subsequently had to take some of its systems offline.
Another successful attack took control of a few electronic billboards in Israel for a short time and used them to post images supporting Gaza. No one claimed responsibility for this attack.
Following is how the attack looked on the CTV billboard with a Palestine flag (screenshot from the Cyber News Telegram channel):
Several groups claimed to have hacked, stolen, and published data from various Israeli entities, including Israeli hotel chains. Most of those claims were not confirmed.
Forward Outlook:
As mentioned earlier, we are currently observing the beginning of three developments that if continued, can lead to increased risks and tension in the cyber battleground. In addition, we see the emergence of more mature cyber actors with highly significant capabilities. Among these are various Russia-affiliated hacktivist groups, Iranian-affiliated groups and ransomware cybercrime groups.
Attention Shift of Russia-Affiliated Hacktivists Groups
Since the first hours of the war, we have observed a gradual shift of attention of major Russian-affiliated hacktivists group like Killnet and Anonymous Sudan away from their regular narrative against Ukraine and Western countries, to an extreme narrative against Israel.
These groups (and groups directly linked with them) post, repost and quote a variety of abusive content against Israel and Israeli interests, and associate and draw parallels between Israel and Zionism and Nazism; a narrative that previously was widely used by such groups about Ukraine.
In the first days of the war, Killnet used Google Translate to post an alleged explanation in Hebrew for the shift in their attention from Ukraine to Israel:
It is worth noting that of all the hacktivist groups, the Russian-affiliated Anonymous Sudan was the first to jump onto the battlefield. They claimed that as early as Saturday morning October 7 at 07:33am, that the Israeli public alarm system Tzeva Adom was down. The group fully committed to the anti-Israeli effort and later announced their successful takedown of the Jerusalem Post site.
In addition, Anonymous Sudan and Killnet opened a shared channel for the purpose of activity against Israel, still without any claims of actual attacks posted there.
Cybercriminals Trying to Leverage the War for Financial Purposes
The war has also drawn financially motivated entities into the cyber battlefield. Ransomed.vc, a ransom group that recently began operations and has had a dozen high-profile victims in the last month, announced that the security situation in the region makes commercial entities more vulnerable to attacks and requested to buy initial access to entities in Israel, Palestine and Iran. The group later posted what they claimed was a healthcare-related data dump of Palestinian patients as an example of what they are looking for.
Iranian Government Affiliated Groups Entering the Battlefield ?
Adl Ali, a hacktivist group that emerged in late September 2022 during widespread protests against the Iranian regime following the death of Mahsa Amini, jumped into the fray on October 10, claiming to target Israeli infrastructure.
The group clearly represents the interests of the Iranian regime and presents itself as “Iran’s freedom-loving youth.” Their primary objectives until now have been to conduct informational operations targeting opposition entities and individuals. The group initially gained attention by asserting that they had obtained documents and chat records through a cyberattack on the Komala Party of Iranian Kurdistan and alleging the party’s involvement in a plot to sabotage the Iranian state in the “Mahsa Amini case.”
Until now, they have focused their efforts on a wide range of targets, including the family of Reza Pahlavi, the son of the last Shah of Iran and a leader of an exiled opposition group; Masih Alinejad, an Iranian-American women’s rights activist; and Nazanin Boniadi, a British actress with Iranian roots known for her activism for Iranian youth and women’s rights.
Currently, there seems to be a shift in their focus, with an announcement that they “launched a cyberattack on the vital infrastructure” of Israel. However, one week later, no specific targets or damage were publicly disclosed.
Conclusion and a look forward
The cyber implications of the Russian incursion into Ukraine and vice versa were significant, underscoring that wars in the digital age can impact a broader spectrum of entities beyond the primary parties involved. Roughly 20 months later, we observe an increase in activity by third-party groups that are taking a stance in the conflict, some of whom have taken measures that impact civilian digital infrastructure.
As the current conflict unfolds, it’s clear that various actors, like Hezbollah and Iran, are evaluating their strategic positions. Cyber warfare is anticipated to be a tool utilized by multiple entities on both fronts, regardless of their direct involvement in the ground conflict.
A question that arises is how entities such as Hamas, facing infrastructural challenges like power outages in the Gaza Strip, will navigate the cyber domain. While they may have operational units outside the Gaza Strip, maintaining consistent cyber operations with challenges at their core locations is indeed a hurdle.
Cyber warfare will undoubtedly play a pivotal role in shaping the trajectory of this conflict. Organizations, regardless of their geographic location, should take this time to enhance their cyber defenses, prioritize system updates, and refine their cybersecurity protocols.
Do’s and don’ts in times of War
A time of regional war and conflict calls for individuals and organization to take extra special care and attention in any online activity.
We are calling for all to remain alert and aware. Here are some basic recommendations for such awareness:
- Awareness: Be aware of any medium and surface you interact with and remain vigilant and smart when receiving messages whether via email, text messages or online. Any message could be malicious or contain a link to malicious malware. Interact only with known senders
- Download software or apps from trusted sources only: Download your apps for either iOS or Android from trusted official sources only. Many threat actors will try and send out their malware disguised as a legitimate app
- Don’t click on unfamiliar links: Never click on links originating from unfamiliar sources, nor should you go online to links you are not familiar with. Pay attention to the URLs, is there anything usual or unfamiliar about them? By taking a minute to look for signs that a website may be fraudulent you can quickly identify its legitimacy.
- Up-to-Date Patches: Keeping computers & software up-to-date and applying security patches, especially those labelled as critical, can help to limit an organization’s vulnerability to attacks as such patches are usually overlooked or delayed too long to offer the required protection.
- Strengthening User Authentication: Enforcing a strong password policy, requiring the use of multi-factor authentication, and educating employees about various attacks designed to steal login credentials are all critical components of an organization’s cybersecurity strategy.




285 comments
cle9se
7q9dhg
0a333l
oipsvt
xcnmeq
3wcapk
1ynlfs
01nwhx
t2qxb8
rsx3se
c4cvyy
vx8h1y
zdigqz
qezikn
Хотите узнать, как заказать реплику AirPods PRO? Мы подскажем.
На промокод 1win собраны лучшие промокоды для увеличения выигрышей.
Все лучшие промокоды для 1win доступны на 1wincodes.ru. Начните выигрывать больше уже сегодня!
Введите промокод 1win казино и получите доступ к дополнительным бонусам и привилегиям.
Найдите самые актуальные предложения с промокод 1win.
В этом магазине можно встретить множество разнообразных аксессуаров.
Получите эксклюзивные привилегии, используя промокод 1вин.
Хотите получить эксклюзивные бонусы? Заходите на 1wincodes.ru и активируйте промокоды для 1win.
Соберите все актуальные промокоды на 1win и начните игру с дополнительными бонусами и привилегиями.
На промокод 1вин собраны самые актуальные предложения и бонусы.
Профессиональное бухгалтерское обслуживание Минск для вашего предприятия.
Наши услуги бухгалтерской фирмы помогут вам в финансовом управлении.
Наши услуги бухгалтерской фирмы помогут вашему бизнесу.
С началом учебного года срочно понадобилось купить школьные принадлежности для ребёнка. На это нужно было 10 тысяч рублей, но моя кредитная история оставляла желать лучшего. На канале https://t.me/s/novue_zaimu я нашёл подборку новых займов на карту. Важно, что эти займы предоставлялись даже с просрочками. Оформив заявку по рекомендациям с канала, я быстро получил деньги и купил все необходимые вещи для школы.
Закажите бухгалтерское сопровождение на uslugi-buhgaltera.by и получите уверенность в отчетности.
Покупая аналоги AirPods PRO по выгодной цене, можно значительно сэкономить.
Мы предоставляем бухгалтерские консультационные услуги для всех видов бизнеса.
Профессиональная консультация бухгалтера Минск поможет вам в решении финансовых вопросов.
Качественные услуги бухгалтера для вашего бизнеса по доступной цене.
Мы предоставляем качественный аудит бухгалтерии и консультации для вашего бизнеса.
Выбирая копию AirPods PRO высокого качества, вы получаете отличное соотношение цены и качества.
Сравните предложения и выберите лучшие аудиторские компании на рынке.
I say tiktoksaver in favour of TikTok video download
Наши бухгалтерские услуги Минск включают комплексное сопровождение бизнеса.
Профессиональное ведение бухгалтерии ООО для вашего бизнеса.
Мы предлагаем бухуслуги для успешного ведения бизнеса.
Лучшие советы по поиску дешевых аналогов AirPods PRO здесь.
Чтобы аудит заказать с гарантией качества, свяжитесь с нами.
Мы предоставляем услуги бухгалтера Минск с профессиональным подходом.
Закажите у нас бухгалтерские услуги РБ и получите надежное обслуживание.
Как избавиться от нежелательных бородавок?
Бородавка на стопе лечение plastica.onclinic.ru .
Выбирайте бухгалтерская компания для надежного бухгалтерского сопровождения.
Мы специализируемся на продаже реплик беспроводных наушников, которые пользуются популярностью.
Опытный бухгалтер для среднего бизнеса с многолетним стажем.
Качественное оказание бухгалтерской помощи обеспечит точность и надежность отчетности.
Используйте промокод 1win, чтобы получить максимальные привилегии при регистрации.
Посетите 1wincodes.ru, чтобы найти все актуальные промокоды и бонусы для 1win.
Узнайте, как получить больше бонусов, используя промокод 1вин.
Для тех, кто ищет бюджетные airpods PRO копия наушники, существует множество вариантов на рынке.
Нужны деньги прямо сейчас? Подписывайтесь на канал срочные займы! Только проверенные МФО и лучшие условия для вас. Получите займ на карту без отказа и без лишних вопросов. Не упустите свой шанс!
Для удобства скачайте приложение скачать акдере и делайте ставки в любое время.
Попробуйте akdere stavka и слоты, чтобы получить максимум удовольствия от игры.
Введите промокод акдере бет на слоты для получения бонусов на игровые автоматы.
Если вы любите взломанные версии, попробуйте скачать акдере приложение взломка.
I utter tiktoksaver in favour of TikTok video download
Попробуйте скачать akdere взлом, чтобы получить доступ к дополнительным функциям.
Индивидуальные дизайны кухонь, которые вдохнут жизнь в ваш дом https://kupitkuhnyu-ot-proizvoditelya.ru/.
Для большего удобства скачайте взлом акдере ставка и пользуйтесь всеми возможностями.
Установите акдере бет приложение, чтобы делать ставки быстро и удобно.
Уникальные методики достижения идеального блеска, поделитесь результатами
Сервис полировки авто http://polish-avto.ru/ .
Если у вас Android, скачать акдере бет на андроид будет идеальным решением.
Если вы любите фриспины, не забудьте скачать акдере фриспины для получения бесплатных вращений.
В казино akdere bet казино вы найдете множество интересных игр и слотов.
Если хотите играть с телефона, попробуйте скачать akdere bet на телефон взломанную версию.
Просто скачать akdere bet на свой смартфон и начинайте делать ставки.
Explore the captivating pictures in this collection – there’s something to delight every viewer! Whether your preference is based on outdoor or indoor picture taking, models showcasing their poses or emotions, you will find various visuals to take pleasure from. Feel absolve to peruse through the edited, whimsical, individual, and group shots too. Naked Grannies Website blend is guaranteed to bring a smile to your face!
Воспользуйтесь промокод akdere bet, чтобы получить бонус при первой ставке.
Новое akdere bet приложение поможет вам делать ставки в любое время и в любом месте.
Такси Сочи аэропорт предлагает комфортный и доступный способ доехать до вашего рейса. Заказывая такси заранее, вы можете избежать стресса, связанного с поисками транспорта в последний момент. Многие компании предлагают фиксированные тарифы, что позволяет заранее знать цену поездки. Это особенно выгодно, если вы путешествуете с большим багажом или детьми. Водители такси в Сочи хорошо ориентируются в городе и окрестностях, обеспечивая быстрое и надёжное прибытие в аэропорт.
Если хотите всегда быть в курсе событий, просто скачать акдере бет на свое устройство.
На платформе akdere bet доступны разнообразные ставки на спортивные события.
News, tech, hobby https://how-tosearch.com/
Не упустите шанс промокод akdere stavka на сегодня 2024 для получения актуальных бонусов.
Для большего удобства скачать akdere и получите доступ ко всем функциям сайта.
Для большего удобства скачать akdere и получите доступ ко всем функциям сайта.
Введите промокод акдере бет на слоты для получения бонусов на игровые автоматы.
Скачайте акдере ставка приложение, чтобы всегда быть на связи с последними спортивными событиями.
Не упустите шанс промокод akdere stavka на сегодня 2024 для получения актуальных бонусов.
Наша команда опытных специалистов обеспечит качественный и профессиональный монтаж вашей кухни https://kupitkuhnyu-ot-proizvoditelya.ru/.
Используйте промокод акдере ставка на слоты для увеличения выигрышей в слотах.
Если вы любите фриспины, не забудьте скачать акдере фриспины для получения бесплатных вращений.
Хотите делать ставки с телефона? Тогда скачать akdere bet на телефон и наслаждайтесь удобством.
Не пропустите шанс промокод акдере бет скачать и получайте бонусы за скачивание приложения.
I despise tiktoksaver seeing that TikTok video download
7qkfjq
Ищете способ расслабиться и получить незабываемые впечатления? Мы https://t.me/intim_tmn72 предлагаем эксклюзивные встречи с привлекательными и профессиональными компаньонками. Конфиденциальность, комфорт и безопасность гарантированы. Позвольте себе наслаждение и отдых в приятной компании.
The mature women in these sexy pics love pleasuring youthful guys, getting smart, and checking out new things during intercourse. Some even get to enjoy themselves in team activities with big dark guys. In addition they enjoy taking control, checking out new positions, and having fun with Nude girls. It’s all about having a blast!
kifw3s
icx4f8
I utter tiktoksaver an eye to TikTok video download
Хотите сделать ставки на бокс и узнать, что прогнозируют эксперты? Добро пожаловать на Octagon Express! Наши аналитики подготовили для вас самые точные ставки на бокс, учитывая все нюансы предстоящих поединков. Узнайте, кто в фаворитах, и сделайте свой выбор, опираясь на профессиональные прогнозы. Подписывайтесь на обновления и выигрывайте вместе с Octagon Express!
Не успели посмотреть бой? Не беда! На Octagon Express вы найдете самые свежие результаты боев ММА. Узнайте, кто вышел победителем, и прочитайте подробные отчеты о каждом поединке. Подписывайтесь на обновления и будьте в курсе всех событий, чтобы не пропустить ни одной важной детали. Следите за всеми результатами вместе с Octagon Express и оставайтесь информированными!
Не успели посмотреть бой? Не беда! На Octagon Express вы найдете самые свежие результаты боев ММА. Узнайте, кто вышел победителем, и прочитайте подробные отчеты о каждом поединке. Подписывайтесь на обновления и будьте в курсе всех событий, чтобы не пропустить ни одной важной детали. Следите за всеми результатами вместе с Octagon Express и оставайтесь информированными!
Hey people!!!!!
Good mood and good luck to everyone!!!!!
Давайте поговорим, мне есть, что сказать по этому вопросу.
Вальєхо Ірен. Подорож книги. Шалак Христина. Нікого https://vsepro.com.ua/aktualni-publikatsii/ немає в лісі. Реймер Малгожата. Болото солодше меду.Лавренішина Анастасія. Люба Жу.
The website https://search-groups.com/ likely offers a lot of useful information and life hacks because it targets a broad audience interested in practical and effective solutions for everyday tasks. These types of tips and tricks tend to attract attention and engagement.
Trust 1win for all your betting needs, available now at 1winbet1.
Visit superagent26 for the best sports betting experience at 1win and enjoy amazing bonuses.
Quick and simple 1win login provided by 1winbet1.
Откройте для себя удивительный мир турецких сериалов на сайте turkvideo.tv. Здесь вы сможете смотреть турецкие сериалы на русском языке, наслаждаясь великолепной озвучкой и высоким качеством. Каждая история, каждая серия захватывает дух и увлекает в незабываемое путешествие. Насладитесь драмами, романтическими историями и приключениями без ограничений. Присоединяйтесь к нашим зрителям и откройте для себя новые эмоции и впечатления от просмотра лучших турецких сериалов на русском языке.
Get started quickly and easily at superagent26 by following the 1win login process.
Many users prefer 1win because of its user-friendly interface and great odds on 1winbet1.
На сайте turkvideo.tv вас ждут самые свежие и захватывающие турецкие сериалы 2024. Погружайтесь в новые истории с великолепной игрой актеров и профессиональной русской озвучкой. Все сериалы доступны бесплатно и в HD качестве, без надоедливой рекламы. Мы гордимся тем, что занимаем первое место в поиске Yandex. Откройте для себя новинки турецкого кинематографа и начните смотреть прямо сейчас на turkvideo.tv!
Join thousands of satisfied bettors on 1win by visiting 1winbet1.
Superagent26 helps you navigate through the 1win login process with ease and confidence.
Enhance your betting strategy by using the resources available at superagent26 for 1win.
Enhance your betting experience with 1win, brought to you by 1winbet1.
Superagent26 guides you through the steps for a smooth 1win login and instant access to games.
Тренажеры для спортзала: купить с бесплатной установкой
тренажер для зала http://trenajeri-dlya-zala.ru/ .
Superagent26 provides a comprehensive tutorial for a flawless 1win login.
Если вы хотите турецкие сериалы смотреть онлайн, заходите на turkvideo.tv. У нас вы найдете широкий выбор сериалов в HD качестве, с русской озвучкой и без назойливой рекламы. Окунитесь в увлекательные истории и насладитесь лучшими сериалами Турции. Мы уверенно занимаем ТОП 1 в поиске Yandex, предоставляя вам только самый качественный контент. Начните смотреть прямо сейчас и откройте для себя мир турецкого кино на turkvideo.tv!
В 2024 году турецкие сериалы обещают быть особенно захватывающими и увлекательными. На сайте turkvideo.tv вы можете смотреть турецкие сериалы 2024 онлайн, наслаждаясь новыми историями и потрясающей актерской игрой. Каждый сериал наполнен эмоциями, драмой и неожиданными поворотами сюжета. Не упустите возможность быть в курсе всех новинок и погрузиться в мир турецкого кинематографа. Начните просмотр прямо сейчас и откройте для себя лучшее, что подготовили турецкие режиссеры в этом году!
Looking for a reliable betting platform? Check out superagent26 and try your luck at 1win.
Reliable 1win login for seamless access on 1winbet1.
Join thousands of satisfied bettors on 1win by visiting 1winbet1.
Enjoy instant access to your favorite games with an easy 1win login guide from superagent26.
Lorem Ipsum has been the industry’s standard dummy text https://placassolaresmalaga2000.es/hnupufh of type and scrambled it to make a type specimen book.
Access your account easily with 1win login on 1winbet1.
Lorem Ipsum has been the industry’s standard dummy text https://impertdesign.pl/gixcw of type and scrambled it to make a type specimen book.
Sign in quickly using 1win login on 1winbet1.
Superagent26 helps you navigate through the 1win login process with ease and confidence.
Explore a wide range of betting markets with 1win on 1winbet1.
Follow superagent26 for the latest updates and news related to 1win login.
Discover exciting betting opportunities at 1win, exclusively on 1winbet1.
Superagent26 provides comprehensive reviews and tips for players at [url=https://superagent26.ru/]1win[/url].
Рекомендую всем, кто ищет смотреть турецкие сериалы 2023 онлайн на русском языке, посетить сайт turkline.tv. Этот сайт лидирует в Google и Yandex, и заслуженно. Все сериалы доступны в HD качестве и абсолютно бесплатно. Удобный интерфейс и широкий выбор жанров делают просмотр еще более приятным. Лично я был очень рад найти такой ресурс и теперь постоянно использую его для просмотра новинок. Турклайн.тв – идеальное место для любителей турецких сериалов на русском языке.
Enhance your betting strategy by using the resources available at superagent26 for 1win.
Ищете, что посмотреть вечером? Обратите внимание на новые турецкие сериалы на turkline.tv. Этот сайт предлагает последние новинки в HD качестве и без рекламы. Вас ждет широкий выбор жанров, и все это совершенно бесплатно. Турклайн.тв – лидер в Google и Yandex, что подтверждает его надежность и популярность. Отличный выбор для любителей турецкого кино.
Explore a wide range of betting markets with 1win on 1winbet1.
I want to show you one exclusive program called (BTC PROFIT SEARCH AND MINING PHRASES), which can make you a rich man!
This program searches for Bitcoin wallets with a balance, and tries to find a secret phrase for them to get full access to the lost wallet!
Run the program and wait, and in order to increase your chances, install the program on all computers available to you, at work, with your friends, with your relatives, you can also ask your classmates to use the program, so your chances will increase tenfold!
Remember the more computers you use, the higher your chances of getting the treasure!
DOWNLOAD FOR FREE
Telegram:
https://t.me/btc_profit_search
Для тех, кто хочет смотреть турецкие сериалы 2023 онлайн, рекомендую turkline.tv. Здесь представлены все новинки 2023 года в HD 1080 качестве и с русской озвучкой. Вы сможете наслаждаться любимыми сериалами без рекламы и абсолютно бесплатно. Турклайн.тв – идеальный выбор для всех поклонников турецких сериалов, предлагая разнообразие жанров и увлекательные сюжеты.
Join superagent26 now and dive into the exciting world of 1win online gaming.
Matt Michael D’Agati functions as the owner of Renewables Worldwide, a Solar Firm in Massachusetts.
A couple of age ago, taking an adventurous journey, Matthew D’Agati stepped into the world of alternative energy, and also in a short experience began effectively selling significant amounts of power, primarily within the corporate industry, partnering with solar farm developers and local businesses in the “architecture” of specific designs.
Ongoing networks in a matter of the profession, guided Matthew to link with a regional start up two a very long time gone, and within a short time, he became their Chief Strategy Officer, overseeing all function and site formation, along with being provided small section possession.
During specific partners and sheer jobs mentality, Matt D’Agati boosted that companionship from a modest to start with-year proceeds to over a 150% raise in arrant sales revenue by year two. Based on that foundation, RW, an veteran soldier-held company, was shaped with quest of offering alternative fuel systems for a more intelligent and more safe future.
More exclusively, realizing there is a specific market in the industry and an improved approach to create benefits, RW’s is one of the few employers in the America to notice on customer obtain, focusing in both industrial and residential solar energy ranch off-take. His or her vision is to initiate a commissions structure on a community-based, statewide, countrywide level, offering various inexhaustible stamina services and products inside the of RW.
This dedication in all sustainable industry continues on to energize and inspire Matt in on going his chase to work with associations that overlap the the exact same of furnishing renewable potential solutions for a a whole lot more eco- friendly outlook. Matthew have their in organization from Hesser College.
Looking into commercial sun-powered opportunities in Massachusetts with Matt dagati.
Портал о здоровье
https://www.rezus.ru и здоровом образе жизни, рекомендации врачей и полезные сервисы. Простые рекомендации для укрепления здоровья и повышения качества жизни.
На сайте turkhit.tv вы найдете турецкие сериалы онлайн на русском языке. Платформа предлагает огромный выбор сериалов на любой вкус: драмы, комедии, боевики и фэнтези. Все сериалы имеют качественную русскую озвучку, что делает просмотр комфортным и приятным.
На сайте представлены как новинки, так и популярные хиты, такие как “Основание Осман” и “Кровавые цветы”. Платформа не требует регистрации или оплаты, что позволяет наслаждаться любимыми сериалами без лишних хлопот. Заходите на turkhit.tv и наслаждайтесь захватывающими историями.
Pedro Gonzalez Lopez https://pedri.prostoprosport-ar.com better known as Pedri, is a Spanish footballer who plays as an attacking midfielder for Barcelona and the Spanish national team. Bronze medalist of the 2020 European Championship, as well as the best young player of this tournament. Silver medalist at the 2020 Olympic Games in Tokyo. At the age of 18, he was included in the list of 30 football players nominated for the 2021 Ballon d’Or.
If you are bored of seeing the same old pics, just take a glance at our other types for something fresh. We’ve plenty of choices to keep you amused and having fun on our website. Therefore, go ahead and browse around – almost always there is more to see with this range of Granny photo!
Lorem Ipsum has been the industry’s standard dummy text https://sigrid-kronenberger.de/kiwtg of type and scrambled it to make a type specimen book.
1win казино — популярная платформа для онлайн азартных игр. Оно предлагает широкий выбор слотов, настольных игр и ставок на спорт в удобном интерфейсе. Бонусы для новых игроков и регулярные акции делают игру выгодной и увлекательной. скачать 1win слоты для установки игровых автоматов и игры в слоты. Стабильная работа сайта и быстрые выплаты делают 1win привлекательным выбором для любителей азарта.
Если вам по душе захватывающие истории о войне, turklife.tv предлагает турецкие сериалы военные. Здесь вы найдете лучшие военные сериалы в HD 1080 качестве и с идеальной русской озвучкой. Разделение по жанрам и годам делает поиск простым и удобным.
Ежедневные обновления гарантируют новые серии каждый день, и всё это бесплатно и без рекламы. Turklife.tv – это лучшее место для любителей военных сериалов. Заходите и погружайтесь в увлекательные военные истории прямо сейчас!
Kyle Andrew Walker https://kylewalker.prostoprosport-br.com English footballer, captain of the Manchester City club and the England national team. In the 2013/14 season, he was on loan at the Notts County club, playing in League One (3rd division of England). Played 37 games and scored 5 goals in the championship.
Medicine information. Effects of Drug Abuse.
can i order cheap tetracycline for sale
Everything trends of drug. Read here.
Lorem Ipsum has been the industry’s standard dummy text https://login-betway-india.com/bgxoojn of type and scrambled it to make a type specimen book.
https://rem-72.ru/remont-kvartir-v-mytishhax/
Мне хотелось сделать ставку на крупный теннисный турнир. Были уверенность и хорошие прогнозы, но денег на ставку не было, а просрочки по другим кредитам портили кредитную историю. Начал искать выход в Яндексе и нашел Телеграм канал займы онлайн на карту малоизвестные мфо на первом месте. Это сразу внушило доверие. На канале были новые МФО, которые давали займы всем без исключения. За 10 минут оформил займ, получил деньги и сделал ставку. Моя ставка выиграла, и я заработал прилично, а также улучшил свою кредитную историю. Всем советую подписаться на этот канал!
Lorem Ipsum has been the industry’s standard dummy text https://baumschuerze.de/frtkqt of type and scrambled it to make a type specimen book.
Если хотите лучшие турецкие сериалы, заходите на turkhit.tv! Мы – первые в Google и Yandex благодаря нашему огромному выбору популярных сериалов. Потрясающее HD качество, профессиональная русская озвучка и отсутствие назойливой рекламы делают наш сайт лучшим для просмотра.
На turkhit.tv вы найдете хиты разных жанров, удобный интерфейс и ежедневные обновления. Откройте для себя мир лучших турецких сериалов прямо сейчас!
Hello!
I want to tell everybody about my experience concerning it security.
I started to looking into how to check all issues of my projects and app and read one article by chance, part of it below:
Full variant here – https://www.nytimes.com/2015/05/13/business/dealbook/owner-of-anonymous-hackers-for-hire-site-steps-forward.html?searchResultPosition=1
Well, after i hired 2-3 professionals hackers and they helped me to do full audit by reasonble cost.
Good luck!
Where to hire hackers
Professional hacker service
Order a hack
Order a hack
Hire hacker
Find a hacker
Rent a hacker
Professional hacker for hire
Ищете лучшие турецкие сериалы? Заходите на turklife.tv! Здесь вы найдете самые свежие новинки 2024 года и другие популярные сериалы в отличном HD 1080 качестве с профессиональной русской озвучкой. На сайте представлены сериалы всех жанров: драмы, комедии, боевики, фэнтези и многое другое.
Каждый день добавляются новые серии, и всё это абсолютно бесплатно и без рекламы в плеере. Turklife.tv – это идеальное место для поклонников турецких сериалов. Заходите и наслаждайтесь лучшими сериалами без лишних хлопот!
Сайт turkhit.tv предлагает турецкие сериалы в хорошем качестве. Здесь каждый день выходят новые серии с качественной русской озвучкой. Забудьте о навязчивой рекламе и наслаждайтесь просмотром. Вы найдете сериалы на любой вкус: мелодрамы, триллеры, боевики.
На сайте доступны как новинки, так и классические сериалы, такие как “Ветреный холм” и “Мехмед: Султан Завоеватель”. Не требуется регистрация или оплата, что делает использование платформы еще проще. Заходите на turkhit.tv и смотрите любимые сериалы в любое время.
I use tiktoksaver an eye to TikTok video download
Обладатели iPhone могут наслаждаться всеми преимуществами мобильного беттинга, если скачать Фонбет на айфон бесплатно. Это приложение предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей. Скачайте его бесплатно и начните делать ставки прямо сейчас.
Для любителей захватывающих боевиков Turklife.tv предлагает турецкие сериалы боевики! Здесь собраны лучшие сериалы жанра, которые держат в напряжении с первой до последней минуты. Все сериалы в HD 1080 качестве и с отличной русской озвучкой.
Сайт ежедневно обновляется новыми сериями, и всё это бесплатно и без рекламы. Turklife.tv – это ваш лучший выбор для просмотра турецких боевиков онлайн. Заходите и наслаждайтесь захватывающими историями прямо сейчас!
Современные технологии позволяют делать ставки на спорт еще удобнее. С Фонбет мобильная вы получите доступ ко всем функциям сайта прямо с вашего мобильного устройства. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Наслаждайтесь миром ставок с приложением Фонбет.
Хотите делать ставки на спорт с вашего айфона? Тогда скачать Фонбет на айфон – это именно то, что вам нужно. Приложение Фонбет разработано специально для устройств Apple и предоставляет пользователям удобный и интуитивно понятный интерфейс. Скачайте Фонбет на айфон и наслаждайтесь широким выбором спортивных событий и возможностью делать ставки в любое время.
Для тех, кто ищет надежное приложение для ставок на спорт, [url=https://fonbet-ajfon-besplatno.ru/]ссылка[/url] предоставляет доступ к лучшему букмекерскому сервису. Скачайте приложение и наслаждайтесь удобным интерфейсом, быстрым доступом к различным спортивным событиям и возможностью делать ставки в любое время и в любом месте. Фонбет предлагает широкий выбор спортивных событий и привлекательные бонусы для своих пользователей.
В один прекрасный день у меня дома произошла авария – потекла труба в ванной. Срочно нужны были деньги на ремонт, а кредитная история у меня была плохая. В Яндексе нашел на первом месте Телеграм канал займы новые онлайн . Это вызвало доверие сразу. На канале был список малоизвестных займов, которые давали деньги всем по паспорту от 18 лет, с выгодными ставками от 0 до 0.8 процента в день. Оформив займ за 10 минут, я получил 30 тысяч и быстро вызвал мастера. Проблему решили моментально. Всем советую подписаться на этот канал!
Обладатели iPhone могут наслаждаться всеми преимуществами мобильного беттинга с приложением Фонбет айфон. Это приложение предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей.
Хотите делать ставки на спорт с вашего айфона? Тогда приложение Фонбет на айфон – это именно то, что вам нужно. Фонбет разработано специально для устройств Apple и предоставляет пользователям удобный и интуитивно понятный интерфейс. Скачайте приложение и наслаждайтесь широким выбором спортивных событий и возможностью делать ставки в любое время.
Обладатели iPhone могут наслаждаться всеми преимуществами мобильного беттинга с приложением Фонбет айфон. Это приложение предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей.
Если вы хотите наслаждаться всеми возможностями лучшего букмекерского приложения, то Фонбет скачать на свой телефон – это отличный выбор. Это приложение предоставляет доступ к большому количеству спортивных событий, где вы можете делать ставки в реальном времени. Фонбет предлагает удобный интерфейс и быструю работу, что делает процесс ставок максимально комфортным. Кроме того, здесь вы найдете различные бонусы и акции для новых и постоянных пользователей.
Для тех, кто хочет делать ставки на спорт, Фонбет скачать бесплатно – это отличная возможность получить доступ ко всем функциям сайта прямо с вашего мобильного устройства. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Наслаждайтесь миром ставок с приложением Фонбет, скачав его бесплатно.
Very nice article and right to the point. I am not sure if this is truly the best place to ask but
do you folks have any ideea where to hire some professional writers?
Thanks 🙂 Escape rooms
Для тех, кто ценит удобство и надежность, сайт предлагает возможность скачать приложение Фонбет. Это приложение позволяет делать ставки на спорт в любое время и в любом месте. Удобный интерфейс, широкий выбор спортивных событий и привлекательные бонусы – все это делает Фонбет лучшим выбором для любителей ставок. Перейдите по ссылке и скачайте приложение прямо сейчас.
Обладатели iPhone могут воспользоваться всеми преимуществами мобильного беттинга, если скачать Фонбет ios. Это приложение предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей.
Хотите делать ставки на спорт с надежным приложением? Тогда источник на скачивание приложения Фонбет – это именно то, что вам нужно. Приложение Фонбет предоставляет пользователям удобный интерфейс, быстрый доступ к результатам матчей и актуальным новостям из мира спорта. Скачайте приложение и начните делать ставки прямо сейчас.
Хотите погрузиться в мир сильных эмоций и глубоких сюжетов? На сайте turkishclub.tv вас ждут турецкие сериалы драмы. Здесь собраны лучшие драматические сериалы, которые тронут ваше сердце и оставят незабываемые впечатления. Просмотр доступен бесплатно и в высоком качестве 720 HD, с профессиональным русским переводом и без рекламы.
Каждый день добавляются новые серии, чтобы вы всегда были в курсе последних событий. Присоединяйтесь к нам и наслаждайтесь лучшими драмами турецкого кинематографа онлайн.
Ищете качественные турецкий сериалы на русском языке смотреть онлайн? Добро пожаловать на turkishclub.tv – лидера в мире турецких сериалов. Здесь вы найдете сериалы всех жанров, от мелодрам до исторических эпопей, все доступно в HD качестве и без назойливой рекламы. Наш сайт предлагает удобный поиск и богатый каталог, позволяющий легко находить любимые сериалы.
На turkishclub.tv вы сможете наслаждаться просмотром в любое удобное время, выбирая сериалы по жанрам и годам выпуска. Присоединяйтесь к тысячам довольных зрителей и откройте для себя мир турецкого кинематографа на нашем сайте. turkishclub.tv – ваш надежный спутник в мире турецких сериалов.
Для тех, кто ищет надежное приложение для ставок на спорт, ссылка предоставляет доступ к лучшему букмекерскому сервису. Скачайте приложение и наслаждайтесь удобным интерфейсом, быстрым доступом к различным спортивным событиям и возможностью делать ставки в любое время и в любом месте. Фонбет предлагает широкий выбор спортивных событий и привлекательные бонусы для своих пользователей.
Ищете бесплатные турецкие сериалы в высоком качестве? Сайт turkishclub.tv предоставляет вам такую возможность! Здесь вы найдете лучшие сериалы всех жанров и годов выпуска, доступные для просмотра без рекламы. Наш сайт позволяет наслаждаться любимыми сериалами бесплатно, не тратя время на регистрацию и подписки.
На turkishclub.tv представлена обширная коллекция турецких сериалов, которые можно смотреть онлайн в любое удобное время. Присоединяйтесь к тысячам зрителей, выбирающих лучшее качество и удобство. Откройте для себя мир турецкого кинематографа с turkishclub.tv и наслаждайтесь просмотром бесплатно!
Для тех, кто ценит удобство и надежность, сайт предлагает возможность скачать приложение Фонбет. Это приложение позволяет делать ставки на спорт в любое время и в любом месте. Удобный интерфейс, широкий выбор спортивных событий и привлекательные бонусы – все это делает Фонбет лучшим выбором для любителей ставок. Перейдите по ссылке и скачайте приложение прямо сейчас.
Обладатели iPhone могут наслаждаться всеми преимуществами мобильного беттинга, если скачать Фонбет на айфон бесплатно. Это приложение предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей. Скачайте его бесплатно и начните делать ставки прямо сейчас.
Для тех, кто хочет делать ставки на спорт, Фонбет скачать бесплатно – это отличная возможность получить доступ ко всем функциям сайта прямо с вашего мобильного устройства. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Наслаждайтесь миром ставок с приложением Фонбет, скачав его бесплатно.
Very interesting info!Perfect just what I was
looking for!?
Ищете надежное букмекерское приложение? Тогда Фонбет скачать на ваше устройство — это то, что вам нужно. Скачав это приложение, вы получите доступ к широкому спектру спортивных событий, удобному интерфейсу и возможности делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей, что делает процесс ставок еще более увлекательным и выгодным.
Lorem Ipsum has been the industry’s standard dummy text https://propcraft.pl/jtvekwv of type and scrambled it to make a type specimen book.
Хотите делать ставки на спорт в любое время и в любом месте? Тогда ссылка на скачивание приложения Фонбет – это именно то, что вам нужно. Приложение Фонбет предоставляет пользователям удобный интерфейс, быстрый доступ к результатам матчей и актуальным новостям из мира спорта. Скачайте приложение и начните делать ставки прямо сейчас.
Для тех, кто хочет наслаждаться всеми возможностями мобильного беттинга без затрат, скачать Фонбет на айфон бесплатно – отличное решение. Приложение Фонбет предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Скачайте Фонбет на айфон бесплатно и получайте удовольствие от ставок.
Если вы хотите использовать все преимущества мобильного беттинга, обязательно скачать приложение Фонбет. С этим приложением вы сможете делать ставки на спортивные события в любое время и в любом месте. Приложение Фонбет отличается простым и удобным интерфейсом, а также быстрым доступом ко всем функциям. Наслаждайтесь захватывающими спортивными событиями и делайте ставки легко и удобно.
Для тех, кто ценит удобство и качество, Фонбет приложение станет незаменимым помощником в мире ставок на спорт. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Скачайте Фонбет приложение и наслаждайтесь всеми преимуществами мобильного беттинга.
Если вы хотите использовать все преимущества мобильного беттинга на вашем iPhone, обязательно скачать Фонбет ios. С этим приложением вы сможете делать ставки на спортивные события в любое время и в любом месте. Приложение Фонбет отличается простым и удобным интерфейсом, а также быстрым доступом ко всем функциям. Наслаждайтесь захватывающими спортивными событиями и делайте ставки легко и удобно.
Для тех, кто ищет надежное букмекерское приложение, сайт предоставляет доступ к лучшему сервису для ставок на спорт. Скачайте приложение Фонбет и наслаждайтесь удобным интерфейсом, быстрым доступом к различным спортивным событиям и возможностью делать ставки в любое время и в любом месте. Фонбет предлагает широкий выбор спортивных событий и привлекательные бонусы для своих пользователей.
Чтобы всегда быть в курсе спортивных событий и иметь возможность делать ставки в любое время, скачать приложение Фонбет на свой смартфон – отличное решение. Приложение Фонбет предлагает пользователям широкий выбор спортивных событий, удобный интерфейс и быстрый доступ к вашим ставкам. Скачав это приложение, вы получите множество возможностей для увлекательной игры и, возможно, крупных выигрышей.
A Attraction of Luxury Fashion
Dress enthusiasts plus luxury buyers often discover themselves captivated through a grace plus status of premium style. From the complex features of one Hermes Birkin to a legendary style of a Chanel 2.55, those items symbolize more than just just fashion—they stand for a good specific standing and exclusivity. However, definitely not everyone may have the funds for towards splurge upon those premium products, that offers brought up to the increasing trend of fake bags. Regarding many, those fakes give one approach up to take pleasure in the splendor regarding high fashion designs without breaking an loan provider.
An surge within popularity concerning fake handbags offers opened up a great intriguing conversation about style, honesty, as well as individual style. Inside this blog post, we all will explore a numerous facets regarding some sort of trend, offering style fans along with a extensive handbook for imitation purses. Through a end, you’ll have a knowledge in order to make advised choices which align themselves along with your values and aesthetics.
Moral as well as Legal Factors regarding Replica Bags
When the idea pertains to fake handbags, 1 regarding an many pressing issues is a honorable and legitimate effects. An production and purchase regarding counterfeit items usually are against the law inside a lot of nations, because that infringes mental residential property privileges. This specific definitely not only has effects on the income of high-end models but also increases inquiries concerning an situations below which these fakes are made.
Fashioning & Integrating Replica Handbags
Integrating fake bags into a closet could prove both trendy also principled. A approach would be to combine high-quality imitations with authentic real articles & additional sustainable eco-friendly style pieces. This not only enhance elevates your total appearance but also also promotes promotes a sustainable apparel cycle.
While styling fake purses, think about the occasion event & your attire. A timeless fake purse could bring an element hint of elegance for a an official ensemble, while a fashionable design could render a relaxed appearance more fashionable. Do not get hesitant to play w/different diverse styles and add-ons to create a unique and personalized style.
Furthermore, taking care for replica handbags is key key to preserve their look appearance & longevity. Regular cleaning and appropriate storage may help maintain your your bags looking fresh plus stylish for longer.
The importance Importance of Informed Buyer Choices
In today’s today’s fashion environment, informed buyer choices are more crucial important than ever. Although imitation bags give a cost-effective substitute to luxury designer pieces, it is key to consider the principled & legitimate implications. By staying mindful of where and & how to you buy imitations, you might enjoy high-end apparel while true to your values values.
It’s additionally essential to remember that one’s individual fashion is not dictated by the brand tags or price value tags. Whether you choose to spend in genuine luxury goods or explore checking out the realm of imitation handbags, the key is to find finding pieces that help you feel feel confident plus fashionable.
Final Thoughts
Fake purses carved out out a special niche within the fashion universe, offering an affordable plus reachable alternative for luxury designer pieces. While they come arrive with their own their unique series of of principled
Associated Apparel Subjects
Discovering the world of apparel doesn’t conclude with copy purses. Here are some extra associated topics that might interest you:
Sustainable Fashion
Delve into the value of sustainability in the style field. Learn about sustainable materials, moral manufacturing techniques, and how to create a sustainable collection.
Retro and Thrift Fashion
Discover the appeal of retro and thrift garments. Find out how to source premium retro items, the benefits of thrift apparel, and advice for integrating these items into your contemporary wardrobe.
Homemade Fashion and Repurposing
Become imaginative with Do-It-Yourself style activities and recycling used garments. Acquire useful tips on changing your wardrobe by creating your own adornments or personalizing present articles to give them a fresh existence.
Style on a Shoestring
Discover how to be trendy without breaking the savings. Uncover strategies for securing great offers, buying wisely during discounts, and making the most of your style resources.
Compact Wardrobes
Grasp the notion of a capsule closet—curating a set of key, versatile articles that can be matched and paired to create various looks. Evaluate the advantages of this simple strategy and how to implement it.
Apparel Trends and Forecasting
Keep ahead of the movement by exploring forthcoming apparel tendencies and sector projections. Understand about pioneering fashionistas, influential apparel events, and the newest essential pieces.
Fashion and Tech
Explore how technology is revolutionizing the apparel sector. Topics involve advanced textiles, online fitting rooms, fashion applications, and the influence of social networks on style marketing and buyer actions.
Body Confidence and Fashion
Examine the link between style and body acceptance. Learn about companies advocating inclusive sizes, the importance of representation in apparel publications, and how to outfit for various figures.
Style History
Take a trip through the history of fashion. Discover different periods, legendary style trends, and how earlier styles continue to shape current apparel.
Style Photography and Blogging
Dive into the world of fashion photography and blogs. Acquire guidance on how to take beautiful fashion photos, begin your own apparel journal, and grow your reach online.
Для любителей ставок на спорт, Фонбет мобайл предлагает отличное решение. Скачав это приложение, вы сможете делать ставки на различные спортивные события прямо с вашего телефона. Приложение Фонбет отличается простым и интуитивно понятным интерфейсом, а также быстрым доступом к результатам матчей и актуальным новостям из мира спорта. Откройте для себя новый уровень ставок с Фонбет.
I say tiktoksaver an eye to TikTok video download
?? ?????? Neon54 ????? ???? ???????? ????? ???? ????? ??? ??????? ??????????, ???????????? ????? ??????? ??? ???????????? ???????? ?????? ????? ??? ??????????. ?? ??? ??????????? ??? ?????????, ?? Neon54 ????????? ??? ???????? ??? ????????? ??? ????????? ???? ?????? ??? ?????????.
?????????? ???????? ??????????
??? Neon54, ?? ?????? ??? ??????????? ????? ??????????, ??? ????????? ???????????? ????? ??? ?? ??? ???????? ?????? ?????????. ?? ??????? ??? ???????????? ?????????? ??????? ?? ?????????? ???????, ?????????, ??? ???????, ??? ?? ??? ???????? ??????? ?? ?????????? ??? ???? ???? ?? ??????? ????????? ?? ???????????? ????????????.
????????? ??????? ??? ?????????
?? ?????? Neon54 ????????? ??? ??? ?? ??????????? ??????? ??? ??? ????????? ???. ??? ?? ??????????? ?????? ?????????????? ??? ??? ???????????? ????????? ??? ?? ??????????? ????????????, ?? ??????? ????? ????? ???? ?? ?????????? ?? ????????????. ???? ??????? ????? ??????????? ?? ??????? ??? ???????? ??? ??? ??????????? ?????.
???????? ??? ??????????
?? Neon54 ????? ?????? ?????? ???? ???????? ??? ??? ??????????. ???????????? ??? ?????????? ??????????? ?????????????? ??? ?? ??????????? ??? ???? ?? ?????????? ??? ?? ????????? ???????? ??? ??????? ????? ??????? ?????????????. ????????, ? ????????? ????? ????????????? ??? ??????????? ??? ??? ??? ?????????? ?????, ???????????? ???? ?????? ???? ??? ????????.
?????????? ???????
? ?????????? ??????? ??? Neon54 ????? ????? ?????? ?? ???????? ???? ??????? ?? ??????????? ??????? ? ???????? ??????????????. ? ????? ??????????? ????? ????????? 24/7 ???? ???????? ??????????, email ??? ?????????, ?????????????? ??? ???? ??????? ?? ???? ??? ?????????? ??? ?????????? ???? ?? ??????????.
??????????
?? ?????? Neon54[/url ????? ? ??????? ??????? ??? ???? ????? ??? ??????? ??????????. ?? ??? ???????? ???????? ??????????, ?? ????????? ???????, ??? ???????? ???????? ??? ??? ?????????? ?????????? ???????, ????????? ??? ???????? ??? ??? ?????? ?? ??????. ???????????? ?? Neon54 ??? ????????? ??? ??????? ???????? ?????? ??????!
Обладатели iPhone могут наслаждаться всеми преимуществами мобильного беттинга, если скачать Фонбет на айфон бесплатно. Это приложение предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей. Скачайте его бесплатно и начните делать ставки прямо сейчас.
?? ?????? Neon54 ????? ???? ???????? ????? ???? ????? ??? ??????? ??????????, ???????????? ????? ??????? ??? ???????????? ???????? ?????? ????? ??? ??????????. ?? ??? ??????????? ??? ?????????, ?? Neon54 ????????? ??? ???????? ??? ????????? ??? ????????? ???? ?????? ??? ?????????.
Здравствуйте! В нашем канале собраны МФО, которые предлагают займы под 0% и с процентной ставкой не выше 0.8% в день. Если у вас плохая кредитная история или были просрочки по кредитам, не переживайте – у нас вы найдете решение. Мы также предоставляем круглосуточную поддержку и полезные советы для всех заемщиков. Подписывайтесь и узнайте, как легко можно получить деньги на лучших условиях!
Для тех, кто ищет надежный источник для ставок на спорт, источник предлагает доступ к лучшему букмекерскому приложению. Скачайте Фонбет и наслаждайтесь удобным интерфейсом, быстрым доступом к различным спортивным событиям и возможностью делать ставки в любое время и в любом месте. Фонбет предоставляет широкий выбор спортивных событий и привлекательные бонусы для своих пользователей.
Хотите делать ставки на спорт с вашего айфона? Тогда приложение Фонбет айфон – это именно то, что вам нужно. Фонбет разработано специально для устройств Apple и предоставляет пользователям удобный и интуитивно понятный интерфейс. Скачайте приложение и наслаждайтесь широким выбором спортивных событий и возможностью делать ставки в любое время.
Хотите делать ставки на спорт с вашего мобильного устройства? Тогда сайт на скачивание приложения Фонбет – это именно то, что вам нужно. Приложение Фонбет предоставляет пользователям удобный интерфейс, быстрый доступ к результатам матчей и актуальным новостям из мира спорта. Скачайте приложение и начните делать ставки прямо сейчас.
Хотите делать ставки на спорт с вашего айфона? Тогда приложение Фонбет на айфон – это именно то, что вам нужно. Фонбет разработано специально для устройств Apple и предоставляет пользователям удобный и интуитивно понятный интерфейс. Скачайте приложение и наслаждайтесь широким выбором спортивных событий и возможностью делать ставки в любое время.
I despise tiktoksaver an eye to TikTok video download
Lorem Ipsum has been the industry’s standard dummy text https://bombayinterior.in/ygjkol of type and scrambled it to make a type specimen book.
Если вы хотите использовать все преимущества мобильного беттинга на вашем iPhone, обязательно скачать Фонбет ios. С этим приложением вы сможете делать ставки на спортивные события в любое время и в любом месте. Приложение Фонбет отличается простым и удобным интерфейсом, а также быстрым доступом ко всем функциям. Наслаждайтесь захватывающими спортивными событиями и делайте ставки легко и удобно.
Для тех, кто ценит удобство и надежность, сайт предлагает возможность скачать приложение Фонбет. Это приложение позволяет делать ставки на спорт в любое время и в любом месте. Удобный интерфейс, широкий выбор спортивных событий и привлекательные бонусы – все это делает Фонбет лучшим выбором для любителей ставок. Перейдите по ссылке и скачайте приложение прямо сейчас.
Современные технологии позволяют делать ставки на спорт еще удобнее. С Фонбет мобайл вы получите доступ ко всем функциям сайта прямо с вашего мобильного устройства. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Наслаждайтесь миром ставок с приложением Фонбет.
Если вы хотите использовать все преимущества мобильного беттинга на вашем iPhone, обязательно скачать Фонбет ios. С этим приложением вы сможете делать ставки на спортивные события в любое время и в любом месте. Приложение Фонбет отличается простым и удобным интерфейсом, а также быстрым доступом ко всем функциям. Наслаждайтесь захватывающими спортивными событиями и делайте ставки легко и удобно.
Если вы хотите использовать все преимущества мобильного беттинга на вашем iPhone, обязательно скачать Фонбет ios. С этим приложением вы сможете делать ставки на спортивные события в любое время и в любом месте. Приложение Фонбет отличается простым и удобным интерфейсом, а также быстрым доступом ко всем функциям. Наслаждайтесь захватывающими спортивными событиями и делайте ставки легко и удобно.
Для тех, кто предпочитает делать ставки на ходу, Фонбет мобильная версия скачать – идеальное решение. Это приложение предлагает пользователям удобный интерфейс и быстрый доступ к различным спортивным событиям. Вы сможете легко управлять своими ставками, отслеживать результаты матчей и получать актуальные новости из мира спорта. Фонбет делает все возможное, чтобы предоставить своим пользователям наилучший опыт ставок через мобильное устройство.
Хотите делать ставки на спорт с вашего мобильного устройства? Тогда сайт на скачивание приложения Фонбет – это именно то, что вам нужно. Приложение Фонбет предоставляет пользователям удобный интерфейс, быстрый доступ к результатам матчей и актуальным новостям из мира спорта. Скачайте приложение и начните делать ставки прямо сейчас.
Для тех, кто предпочитает делать ставки на ходу, Фонбет мобильная версия скачать – идеальное решение. Это приложение предлагает пользователям удобный интерфейс и быстрый доступ к различным спортивным событиям. Вы сможете легко управлять своими ставками, отслеживать результаты матчей и получать актуальные новости из мира спорта. Фонбет делает все возможное, чтобы предоставить своим пользователям наилучший опыт ставок через мобильное устройство.
Ищете надежное букмекерское приложение? Тогда Фонбет скачать на ваше устройство — это то, что вам нужно. Скачав это приложение, вы получите доступ к широкому спектру спортивных событий, удобному интерфейсу и возможности делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей, что делает процесс ставок еще более увлекательным и выгодным.
Хотите всегда быть в курсе спортивных событий и иметь возможность делать ставки в любое время? Тогда Фонбет приложение – это то, что вам нужно. С этим приложением вы сможете следить за результатами матчей, делать ставки и получать актуальные новости из мира спорта. Фонбет предоставляет своим пользователям удобный интерфейс и быстрый доступ ко всем функциям, что делает процесс ставок максимально комфортным.
Современные технологии позволяют делать ставки на спорт еще удобнее. С Фонбет мобильная вы получите доступ ко всем функциям сайта прямо с вашего мобильного устройства. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Наслаждайтесь миром ставок с приложением Фонбет.
I use tiktoksaver for TikTok video download
Для тех, кто ценит удобство и качество, Фонбет приложение станет незаменимым помощником в мире ставок на спорт. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Скачайте Фонбет приложение и наслаждайтесь всеми преимуществами мобильного беттинга.
Хотите всегда быть в курсе спортивных событий и иметь возможность делать ставки в любое время? Тогда Фонбет приложение – это то, что вам нужно. С этим приложением вы сможете следить за результатами матчей, делать ставки и получать актуальные новости из мира спорта. Фонбет предоставляет своим пользователям удобный интерфейс и быстрый доступ ко всем функциям, что делает процесс ставок максимально комфортным.
Meds information leaflet. Cautions.
where can i buy zofran prices
Best trends of drugs. Get here.
Если вы ищете надежное приложение для ставок на спорт, то приложение Фонбет на айфон – это то, что вам нужно. Оно предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Фонбет также предлагает привлекательные бонусы и акции для своих пользователей.
Современные технологии позволяют делать ставки на спорт еще удобнее. С Фонбет мобильная вы получите доступ ко всем функциям сайта прямо с вашего мобильного устройства. Это приложение предлагает широкий выбор спортивных событий, удобный интерфейс и возможность делать ставки в любое время и в любом месте. Наслаждайтесь миром ставок с приложением Фонбет.
Доверьте нам создание кухни, которая станет сердцем вашего пространства https://tovudyi4kuhnyanazakaz.ru/.
Получите фрибет на сумму до 3000 рублей, используя Pari промокод на фрибет при регистрации на сайте компании Pari. Не упустите шанс воспользоваться выгодными предложениями!
Для тех, кто хочет наслаждаться всеми возможностями мобильного беттинга без затрат, скачать Фонбет на айфон бесплатно – отличное решение. Приложение Фонбет предоставляет пользователям удобный интерфейс, быстрый доступ к различным спортивным событиям и возможность делать ставки в любое время и в любом месте. Скачайте Фонбет на айфон бесплатно и получайте удовольствие от ставок.
Получите фрибет на сумму до 3000 рублей, используя Pari промокод на фрибет при регистрации на сайте компании Pari. Не упустите шанс воспользоваться выгодными предложениями!
Lorem Ipsum has been the industry’s standard dummy text https://skybet365.es/kdhmk of type and scrambled it to make a type specimen book.
Для тех, кто ищет надежное букмекерское приложение, сайт предоставляет доступ к лучшему сервису для ставок на спорт. Скачайте приложение Фонбет и наслаждайтесь удобным интерфейсом, быстрым доступом к различным спортивным событиям и возможностью делать ставки в любое время и в любом месте. Фонбет предлагает широкий выбор спортивных событий и привлекательные бонусы для своих пользователей.
Lorem Ipsum has been the industry’s standard dummy text https://prodottinautica.it/eowmawb of type and scrambled it to make a type specimen book.
Воспользуйтесь промокод Парибет, чтобы получить эксклюзивные бонусы и фрибеты при регистрации. Откройте для себя лучшие акции на сайте компании Парибет.
Для тех, кто предпочитает делать ставки на ходу, Фонбет мобильная версия скачать – идеальное решение. Это приложение предлагает пользователям удобный интерфейс и быстрый доступ к различным спортивным событиям. Вы сможете легко управлять своими ставками, отслеживать результаты матчей и получать актуальные новости из мира спорта. Фонбет делает все возможное, чтобы предоставить своим пользователям наилучший опыт ставок через мобильное устройство.
Активируйте промокод Pari при регистрации и получите скидки на первые депозиты. Наслаждайтесь выгодными ставками с букмекерской конторой Pari.
Ищете лучшее букмекерское приложение для мобильных ставок? Тогда переходите по ссылка и скачайте Фонбет прямо сейчас. Это приложение предлагает пользователям удобный интерфейс, быстрый доступ к широкому спектру спортивных событий и возможность делать ставки в любое время и в любом месте. Скачайте приложение и получите доступ к лучшему опыту ставок с мобильного устройства.
Наша транспортная компания предлагает грузоперевозки из Москвы в Санкт-Петербург по доступным ценам. Узнайте больше о наших услугах на сайт.
Если вам нужно перевезти груз из Москвы в Санкт-Петербург, обратитесь к нам. грузоперевозки Москва Санкт-Петербург выполняются профессионалами.
Узнайте стоимость грузоперевозки Москва Санкт-Петербург и закажите услуги нашей транспортной компании уже сегодня.
Мы предлагаем услуги по ведение учета для бизнеса в Минске. Узнайте больше о наших услугах и ценах.
Узнайте больше о наших услугах по ремонт бытовой техники в Москве на сайте и закажите мастера на дом.
Если вам нужен ремонт бытовой техники в Минске, обратитесь к нам. Мы предлагаем качественные услуги на дому.
Если вам нужен качественный ремонт бытовой техники на дому, зайдите на сайт для получения информации о мастерах и их услугах.
На деньги в долг Витебск вы найдете лучшие предложения по займам в Беларуси. Узнайте, как срочно получить деньги наличными или на карту.
На сайт вы найдете лучшие предложения по займам и кредитам в Беларуси. Узнайте, как быстро получить деньги на карту без справок.
Если вам срочно нужны деньги в долг, зайдите на сайт для получения информации о потребительских кредитах и займах в Беларуси.
На деньги в долг Минск вы найдете лучшие предложения по займам в Беларуси. Узнайте, как срочно получить деньги наличными или на карту.
I utter tiktoksaver seeing that TikTok video download
Discover mature-naked.com/old-woman-red-pictures/ intended for steamy content presenting mature women who exude confidence plus seduction. These experienced beauties fearlessly possess their sensuality throughout stunning imagery. With years of knowledge under their belt, these mature foxes own a mastery within the art regarding seduction. Just like a good wine, they have got just grown more daring and alluring using age. Prepare to be able to be captivated by way of a insatiable passion plus adventurous spirit — you’ll be remaining craving more.
I realize exactly where an individual should go if you’re into very hot pics of NUDE MATURE WOMEN in the buff. This collection is usually packed with attractive shots of mature women who understand how to affect a pose. They’ll definitely catch your eye with their confident and enchanting looks. Get prepared to dive directly into a world involving captivating nude pictures of mature women that will leave an individual wanting more.
Откройте для себя новые гастрономические горизонты и дизайнерские возможности https://kitubeu2kuhnyanazakaz.ru/.
Милфы и порно с актёрами с маленькими пенисами ждут тебя
Приветствую. Подскажите, где почитатьполезные блоги о недвижимости? Сейчас читаю https://permopaint.ru
Большие сиськи и отменное лесбийское порно без подписки, смотри онлайн
Воспользуйтесь Pari промокод на фрибет для получения дополнительных бонусов и фрибетов при регистрации. Откройте для себя все акции и предложения от Pari.
Стоимость согласования перепланировки помещения в Москве может варьироваться в зависимости от сложности проекта и требуемых процедур. Наша компания предлагает доступные и прозрачные цены, что позволяет вам планировать бюджет без неожиданных расходов.
Чтобы узнать точную стоимость согласования перепланировки помещения в москве, свяжитесь с нашими специалистами. Мы предоставим вам подробную информацию и проконсультируем по всем вопросам, связанным с процессом согласования. Доверяя нам, вы получаете качественное и профессиональное обслуживание.
Наша компания предоставляет услуги грузоперевозки Москва Санкт-Петербург по выгодным ценам. Мы гарантируем качество и надежность.
Ну, кто бы мог подумать, что для того, чтобы передвинуть стену на пару метров, нужен целый проект перепланировки. Ведь зачем просто наслаждаться новым пространством, когда можно углубиться в увлекательный мир бумажной волокиты и архитектурных чертежей?
Наша компания с радостью предоставит вам все необходимые документы и согласования, чтобы вы могли почувствовать себя настоящим проектировщиком. Давайте сделаем это вместе и насладимся каждым этапом бюрократической эпопеи!
Lorem Ipsum has been the industry’s standard dummy text https://prodottinautica.it/mrzdkvm of type and scrambled it to make a type specimen book.
Наша компания предоставляет услуги грузоперевозки Москва Санкт-Петербург по выгодным ценам. Мы гарантируем качество и надежность.
Согласование перепланировки квартиры требует тщательной подготовки и внимания к деталям. Наша компания предоставляет полный спектр услуг по согласованию перепланировок, начиная с разработки проекта и заканчивая получением всех необходимых разрешений.
Обратившись к нам за услугой согласование перепланировки квартиры, вы получите профессиональную помощь на каждом этапе процесса. Мы обеспечим быстрое и качественное согласование, минимизируя ваши затраты времени и усилий.
Bienvenido a milfsdesnudas.com, tu paraГso pra admirar a todas las MILFs mГЎs calientes y sensuales! Durante este lugar para placer, descubrirГЎs una colecciГіn Гєnica de imГЎgenes de MILFs desnudas que lo volverГЎn loco. Las siguientes divas maduras not any tienen reparos en mostrar su sensualidad en cada desnudos., posando con desafГo y exhibiendo sus irresistibles curvas. PrepГЎrate para sumergirte durante un mundo para lujuria, donde estas mujeres experimentadas estan informados sobre cГіmo encender sus fantasГas mГЎs secretas.
доставка грузов Москва Петербург с нашей транспортной компанией — это быстро, надежно и по разумной цене.
ведение бухгалтерского учета включает в себя не только обработку данных, но и налоговый учет. Узнайте больше о наших услугах и ценах.
ремонт бытовой техники в Москве с гарантией качества и по выгодным ценам. Обратитесь к нам для получения услуг.
Who Our Device is For: Who We Can Assist
The vibration balancing and analysis devices from Vibromera are intended for various specialists and industries dealing with the upkeep of optimal performance in rotating machinery.
This includes various types of machines and mechanisms, from industrial fans, pumps, and compressors to complex turbomachinery and automotive engines.
Let’s explore the primary categories of users and applications where our device will be an essential tool.
Centrifuges operate at high speeds , making perfect balance essential for safety and accurate results. Centrifuge balancing services carefully detect and correct imbalances, maximizing equipment performance and ensuring reliability.
Production and Maintenance Firms
The main target for our devices includes companies involved in the manufacturing, maintenance, and repair of different types of rotating equipment.
This group encompasses manufacturers and service centers that focus on pumps, fans, electric motors, turbines, and other machinery.
Our device enables precision dynamic balancing on site, greatly simplifying maintenance and boosting production efficiency.
Power Companies
Thermal and nuclear power plants, as well as other energy companies using turbogenerators, boilers, high-power fans, and rotating machinery, can significantly boost the reliability and lifespan of their units by employing our balancing device.
Мы предлагаем услуги по ремонт бытовой техники в Москве быстро и качественно. Узнайте адреса и телефоны на сайте.
Если вам нужен ремонт бытовой техники, наша мастерская бытовой техники предлагает лучшие услуги в Москве. Все адреса и телефоны доступны на сайте.
Взять деньги в долг Витебск можно легко и быстро. Посетите наш сайт для получения информации о займах и кредитах в Витебске.
деньги в долг Минск предлагает быстрые займы и кредиты на выгодных условиях. Узнайте, как получить деньги в Минске без справок.
Оформить деньги в долг Минск можно легко и быстро онлайн. Узнайте больше о процентах и условиях получения займов в Беларуси.
На деньги в долг Минск вы найдете информацию о лучших кредитных предложениях в Минске. Получите деньги быстро и без лишних документов.
Lorem Ipsum has been the industry’s standard dummy text https://willarybaki.pl/ppmsvti of type and scrambled it to make a type specimen book.
Meds information for patients. Cautions.
where buy generic chlorpromazine without a prescription
Actual about drug. Read here.
Промокод Mostbet при регистрации. Промо-код встречается на просторах сети достаточно часто. Букмекер использует его для привлечения новых игроков в индустрию ставок, но преимущество предоставляется и новому игроку. После того как он совершит первый депозит, на его бонусный счёт поступит аналогичная сумма, до 35000 рублей. промокод для мостбет Данный вид бонус-кода также популярен в поиске. Указывать его надо в купоне для совершения ставки. Промокод Mostbet на ставку практически невозможно найти в бесплатном доступе. Он вручается игрокам индивидуально.К примеру, компания промокодов. В данном разделе подробно расписан процесс получения.
грузоперевозки Москва Санкт-Петербург с нашей транспортной компанией — это гарантия своевременной и безопасной доставки вашего груза.
Чтобы установить приложение, нужно ak dere stawka скачать с официального сайта. Процесс загрузки и установки прост и понятен.
Сегодня у вас есть возможность использовать промокод Фонбет на сегодня бесплатно и получить бесплатные бонусы. Активируйте промокод при регистрации и наслаждайтесь всеми преимуществами, которые он предлагает. Поспешите, предложение ограничено!
Ищете, где срочно взять деньги? деньги в долг Минск предлагает выгодные условия займов и кредитов в Минске.
Наши кухни не просто мебель, это произведения искусства, наполненные вдохновением и инновациями https://guzywia4kuhnyanazakaz.ru/.
деньги в долг Минск предлагает быстрые займы и кредиты на выгодных условиях. Узнайте, как получить деньги в Минске без справок.
Lorem Ipsum has been the industry’s standard dummy text https://konkretmatka.pl/hjpmuf of type and scrambled it to make a type specimen book.
Наши услуги по доставка грузов Москва Петербург — это гарантия качества и доступной стоимости. Закажите у нас уже сегодня.
Секреты успешного арбитража трафика, для увеличения вашего дохода.
Как начать зарабатывать на арбитраже трафика с нуля, даже если вы новичок в этом деле.
Как выбрать подходящие источники трафика для арбитража, для оптимизации конверсии и увеличения прибыли.
Как создать высокоэффективные рекламные кампании для арбитража трафика, которые принесут вам стабильный доход.
Как получить стабильный доход от арбитража трафика без финансовых потерь, с использованием проверенных методов и подходов.
арбитраж паблишеры http://www.traffic-arbitrage.com .
Lorem Ipsum has been the industry’s standard dummy text https://amaterasuspa.pl/eswcz of type and scrambled it to make a type specimen book.
BesГ¶k vГҐr fantastiska webbplats och upptГ¤ck de mest sensuella porrgallerierna, bilderna och fotona – allt helt gratis! Vi lГҐter ej nГҐgon annan definiera vad som Г¤r bГ¤st fГ¶r burrow nГ¤r det kommer till sexuellt innehГҐll mogenporrbilder.com/. VГҐra producenter och leverantГ¶rer av de grymaste vuxenbilderna och fotona vГ¤ljer personligen lace sina favoriter fГ¶r att dela med sig till get. Med miljontals alternativ tillgГ¤ngliga Г¤r e upp till drill down att avgГ¶ra vilka som passar pГҐ bГ¤sta sГ¤tt fГ¶r dina Г¶nskemГҐl. Vi fГ¶rstГҐr att varje persons preferenser skiljer sig ГҐt, sГ¤rskilt nГ¤r e handlar om sexuell attraktion. Oavsett om du fГ¶redrar Г¤kta amatГ¶rflickor i down and dirty sexgallerier eller porrbilder, eller om du hellre ser nakenbilder audio-video kГ¤ndisar – ni har nГҐgot pga alla. Vi respekterar att vissa audio-video vГҐra anvГ¤ndare inte Г¤r intresserade utav komplicerade storylines elr avancerad produktion, medan andra krГ¤ver specifika handlingar fГ¶r att lyckas bli upphetsade. Oavsett vad du kikar runt efter, sГҐ existerar det hГ¤r hos oss pГҐ vГҐr sajt.
s80lul
aro5lb
Наше предприятие осуществляет строительство домов , от проекта, и под ключ, как в Санкт-Петербурге, так и Ленинградской области. Специалисты нашей организации, не только разработают грамотный проект, но и смогут воплотить его в жизнь, проложив внутренние коммуникации и осуществив отделку. Наши профессионалы построят лучшие дома, согласно имеющимся типовым проектам или же по индивидуальному заказу клиента.
An effective SEO company for promoting your website, professional help in the field of SEO.
How to make the right choice of an SEO agency, tips from experts.
Why you should turn to SEO professionals, what results you can achieve.
Top SEO companies to work with, customers’ experience.
Why an SEO company is necessary for your business, major benefits.
amazon seo marketing http://www.seorg-seo.com .
I use tiktoksaver seeing that TikTok video download
Lorem Ipsum has been the industry’s standard dummy text https://sigma-radomsko.pl/npmwlp of type and scrambled it to make a type specimen book.
Lorem Ipsum has been the industry’s standard dummy text https://hostindiaa.in/jpkgk of type and scrambled it to make a type specimen book.