Home users allocated those IPs find themselves stranded in “CAPTCHA hell”
Barracuda, a leading provider of cloud-first security solutions, has unveiled a new Threat Spotlight that shows how in the first six months of 2023, bad – or malicious – bots used residential IP addresses to launch attacks without being caught by the security blocks put on known malicious IPs. In many cases, the people who used or were later allocated those IPs ended up in “CAPTCHA hell,” unable to pass checks from Google or Cloudflare because their IP triggered a red flag as having been used for malicious activity.
Bots are software programs that move around the web performing automated tasks like search engine crawling. Barracuda researchers track the prevalence and behavior of good and bad bots from year to year.
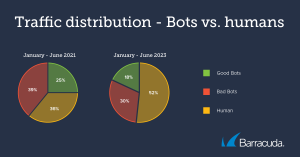
Data for the first half of 2023 shows that nearly half (48%) of total global internet traffic was made up of bots, and most of this was down to bad bots. These complex computer programs are designed to cause mischief and harm, at speeds and volumes that human attackers couldn’t match.
And while in 2021, the bad bot landscape was dominated by swarms of “retail bots,” sent out to hunt for scarce and sought-after sneakers and toys to resell at a profit, in 2023, bad bots are often being used for more advanced attacks.
Armed with millions of common username and passwords, the bad bots are being sent out across the internet with the aim of compromising email accounts – particularly those they can reach through vulnerable application programming interfaces (APIs) – by bashing them with countless combinations of usernames/passwords until they get the one that works.
APIs are a growing target for cyberattack because they are relatively under-protected and used extensively for automated processes and communications. Examples of applications that use APIs to access emails and inboxes include email marketing applications that send and track bulk or personalized emails to potential or existing customers, as well as applications to manage, verify and automate emails.
“For the organizations targeted by these bots, a combination of under-secured APIs, weak authentication and access policies, and a lack of bot-specific security measures – such as limiting the volume and speed of inbound traffic leave them vulnerable to attack,” said Tushar Richabadas, Principal Product Marketing Manager, Applications and Cloud Security at Barracuda. “Organizations can be overwhelmed due to the sheer number of solutions required to stop bots, but the good news is that solutions are consolidating into Web Application and API Protection (WAAP) services that identifies and stops bad bots.”
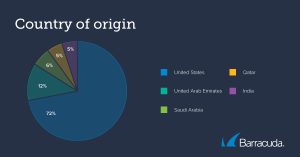
The research also shows that in the first half of 2023, North America was the source of 72% of bad bot traffic. Roughly two-thirds (67%) of bad bot traffic came from hosting providers, including the two large public clouds: AWS and Azure, which skews the geographic data toward North America. The next most prevalent regions are the United Arab Emirates (12%), Saudi Arabia (6%), Qatar (5%), and India (5%).
For further information – including the best defenses against bot attacks, check out the blog at https://blog.barracuda.com/2023/10/18/threat-spotlight-bad-bot-traffic-changing.
About Barracuda Networks
At Barracuda, we strive to make the world a safer place. We believe every business deserves access to cloud-first, enterprise-grade security solutions that are easy to buy, deploy, and use. We protect email, networks, data, and applications with innovative solutions that grow and adapt with our customers’ journey. More than 200,000 organizations worldwide trust Barracuda to protect them — in ways they may not even know they are at risk — so they can focus on taking their business to the next level. For more information, visit barracuda.com.
Barracuda Networks, Barracuda and the Barracuda Networks logo are registered trademarks or trademarks of Barracuda Networks, Inc. in the U.S. and other countries. Other trademarks are the property of their respective owners.



